The 4 Key Features a Bank's Document Collection Platform Must Have
In nearly every industry, the pace of digital operations has accelerated during the last two years. Despite their traditionally risk-averse and...

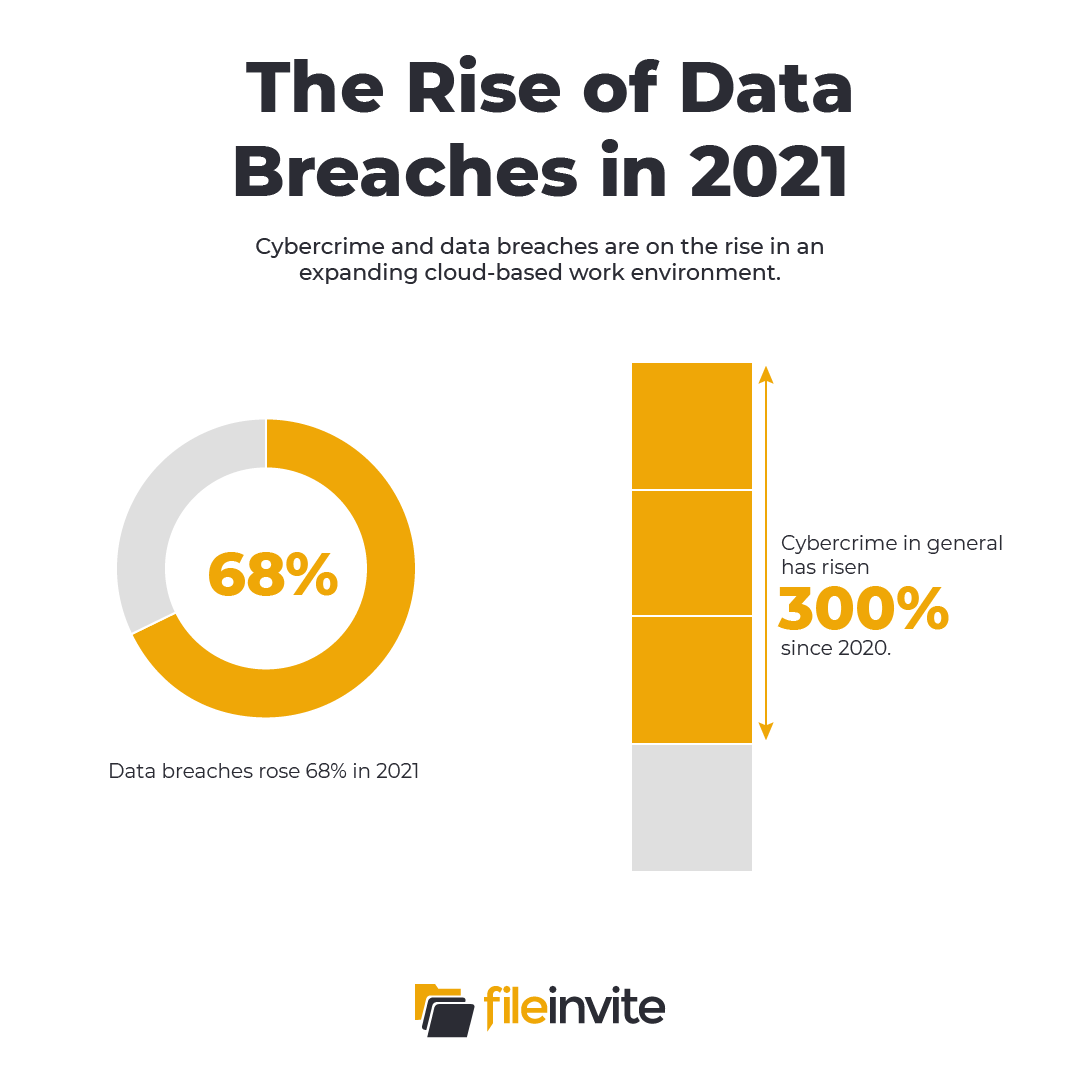
Data breaches are on the rise. Incident reports jumped by 68% in 2021, marking the highest single-year increase on record. The trend in data breaches tracks a generalized surge of 300% in cybercrime since the start of the Covid-19 pandemic in 2020.
For most industry experts, this crimewave has a relatively simple explanation. Businesses shifted to remote work during temporary pandemic restrictions and, in the process, brought terabytes of sensitive information online coupled with millions of new remote access points. In effect, there are more attacks on private data now because there are more targets than ever before.
At the same time, the number of businesses that handle sensitive personal data – either as cloud storage hosts or as providers of Software-as-a-Service (SaaS) – has grown by similar leaps and bounds. In 2022, more than half of global businesses – around 56% – are running at least half their workloads in the cloud. In the SaaS market, nearly 99% of businesses now report using at least one service in their day-to-day operations, driving a sustained compound annual growth rate of 18% for the industry as a whole.
For service providers, these trends combine to set an all-time premium on verified security integrity. To meet the growing demand for standardized security credentials, the American Institute of CPAs (AICPA) has developed a suite of voluntary compliance standards businesses can use to certify their trustworthiness to clients. These standards – known as System and Organization Controls (SOC) – have several levels and types. For banks and financial organizations, SOC 2 Type 2 compliance has become the gold standard for demonstrating a company’s adherence to IT best practices and privacy controls.
The AICPA offers three levels of SOC audits and reports performed by licensed CPA firms.
In these levels, two types specify how the audit was performed.

The SOC 2 Type 2 combination applies the five Trust Services Criteria in a sustained process audit. These are:
To demonstrate Type 2 compliance, companies not only need to demonstrate effective security controls at the design level for these criteria, they must also prove their ability to maintain sustained compliance. Type 1 audits are snapshots of a system at a single point in time. Type 2 audits capture processes in motion, and even brief lapses in standards can result in complications.
For this reason, Type 2 compliance provides potential clients with an order of magnitude greater confidence. At the same time, it is significantly harder to demonstrate and requires firm organizational adherence to best practices.
Here are four steps to take to begin SOC 2 Type 2 compliance in your organization.
Because Type 2 audits occur over an extended period, it is critical not to begin the process until you are ready. Unanticipated vulnerabilities or substandard practices may reset the clock months into the process. To help companies mitigate the risk of discovering problems after the fact, many licensed CPA firms will perform SOC readiness assessments. These assessments identify areas for improvement in key controls and where a company’s ability to monitor and report on their processes may be lacking.

Although half of IT executives identify the protection of sensitive data as their organization’s top security priority, fewer than half believe that cybersecurity issues are well understood or properly prioritized at the boardroom level. CISOs can face an uphill battle trying to secure sufficient budgets for staff and training when costly breaches haven’t happened yet. Long-term SOC 2 Type 2 compliance will require a top-down understanding of security as an investment rather than stop-loss.
Alert fatigue has increasingly become the norm in network security. The average security team fields more than 11,000 firewall and intrusion detection system (IDS) alerts every day. While the majority – 76% – of these alerts are false positives, manually investigating them takes more time than most security teams have and potential breaches get backlogged in the system. To demonstrate continuous, gap-free compliance, you need to develop in-house security practices that keep your dwell times – the time a potential breach remains undetected – to a minimum.

66% of small to medium-sized businesses report experiencing a cyberattack in the last twelve months. Auditing organizations understand that nearly everyone’s data becomes a target at some point. What matters most to auditing organizations is your transparency. Your own incident reports should demonstrate in detail how your systems were reasonably prepared and how your established security protocols were applied.
Secure Data Collection for Faster Turnaround Times with FileInvite
FileInvite enables accelerated data and document collection through client portals with bank-grade, SOC 2 Type 2 compliant security. As banking institutions feel the pressure to perform faster and deliver an increasingly competitive standard of customer satisfaction, FileInvite ensures that your organization can adopt time-saving automation technologies without compromising security standards.
To learn more and request a demo, visit FileInvite today.

In nearly every industry, the pace of digital operations has accelerated during the last two years. Despite their traditionally risk-averse and...

Following steep declines in 2020 and 2021, commercial lending is back on the rise, with total lending volume in the U.S. having recouped two-thirds...

In the last two years, the global shift to remote work has precipitated major changes in the methods and targets of cybercrime. As workloads moved to...