With 3.35% of the global market share, Microsoft Outlook is the third-most-popular email client worldwide. As the default client for Windows and Office 365, Outlook accounts for a higher percentage of business emails than strictly personal communications. Because emails and attachments that contain customer personally identifiable information (PII) now fall under the authority of the enhanced FTC Safeguards Rule, businesses should regulate the use of Outlook to exchange sensitive information and provide their employees with guidelines for sufficiently securing email contents.
Although the FTC conceded in November last year to delay enforcement of the Safeguards Rule until June 2023, many businesses in regulated industries are still struggling to bring their information security practices up to standard. Workplace reliance on email attachments to exchange documents remains a major hurdle. Even though the most widely used email clients – Apple, Gmail, and Outlook – have features for various encryption protocols, most users are unaware of them.
This blog post explains encryption options in Outlook and their pros and cons concerning the Safeguards Rule.
Encrypting Email in Outlook
Users can encrypt emails in Outlook in four ways. Note that options 3 and 4 are only available to users with Office 365 Enterprise E3 licenses.
1. Transport Layer Security (TLS)
Like Gmail, Outlook uses standard Transport Layer Security (TLS) to encrypt outgoing emails. However, TLS only secures email contents in transit to prevent interception.
As users must re-encrypt opened emails to secure them in storage, TLS alone does not satisfy the requirements of the Safeguards Rule.
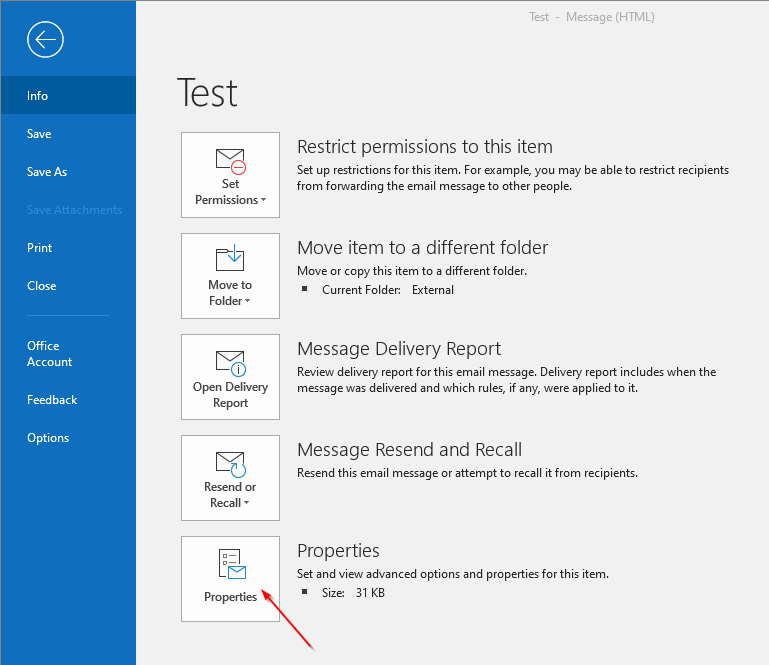
Users should also be aware that Outlook prioritizes message delivery over encryption. This means that when Outlook attempts to send a TLS-encrypted email to an account that does not support TLS version 1.2 or higher, the email does not encrypt and transits in plain text. To check if a received email is encrypted:
- Double-click the email in the inbox, open the Info menu, and select Properties.
- Properties contain the raw message header. Copy the header into a word processor to enable search.
- Search “TLS.” If the header contains a TLS identifier such as “TLS1.2” or TLS1.3,” the email was delivered with encryption.
2. Secure/Multipurpose Internet Mail Extension (S/MIME)
S/MIME is a popular public-key encryption format. Only when deployed with a digital signature, does S/MIME provide end-to-end encryption in compliance with the Safeguards Rule. Outlook supports the use of S/MIME, but users must add a signing certificate to their keychain to enable it.
To encrypt an email with S/MIME in Outlook:
- Open a new message and select the Options tab.
- Select Encrypt to choose permission settings.
- Select Encrypt with S/MIME.

To add a signing certificate for an outgoing email:
- Open Trust Center under the File menu and navigate to Trust Center Settings.
- Select Email Security on the left panel.
- Select the Settings drop-down menu next to Default Settings.
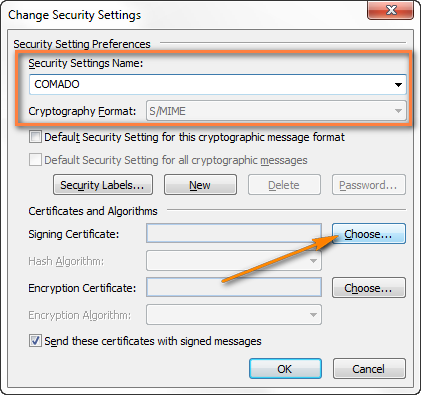
- In the Change Security Settings window, select Choose to the right of the Signing Certificate.
- Click the certificate name, enter the associated password, and click OK.
3. Office 365 Message Encryption (OME): Encrypt-Only
Users with Office 365 enterprise-level accounts can use Microsoft’s client-side encryption and certificate management technology. OME employs 256-bit Advanced Encryption Standard (AES), the highest grade encryption format, and is suitable for use in business operations subject to the Safeguards Rule.
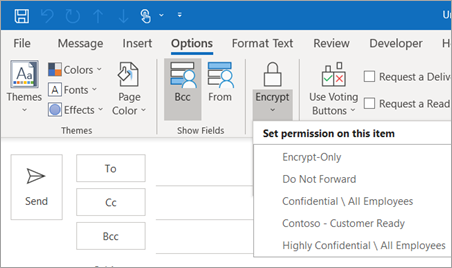
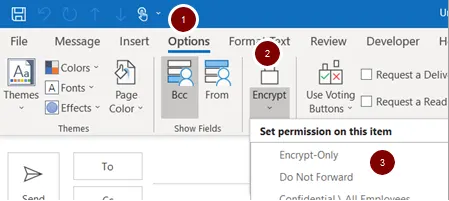
To encrypt a message:
- Open a new message and select the Options tab.
- Select Encrypt to choose permission settings.
- Select Encrypt-Only.
Under the Encrypt-Only setting, recipients cannot disable encryption, but they can forward and download emails and attachments without restriction. For this reason, users should exercise caution when choosing Encrypt-Only recipients.
4. Office 365 Message Encryption (OME): Do Not Forward
To apply additional security controls for OME, follow the steps above but choose Do Not Forward instead of Encrypt-Only. The Do Not Forward permission setting applies AES encryption and disables the Forward and Print buttons on the receiving end. Do Not Forward messages are effectively read-only communications and ensure the greatest degree of sender ownership for Outlook emails.
Securely Share Sensitive Documents with FileInvite
Drafting and enforcing information security policies for email use that ensure Safeguards compliance is a risky venture for businesses in regulated industries. Even with comprehensive policies and training, accidental oversight may still result in data breaches and expose an organization to punitive action and loss of client trust. The most reliable way to mitigate the risk of data breaches is to adopt technologies that are secure by design rather than configuration.
FileInvite’s automated document collection platform provide an efficient single-pane-of-glass solution to the challenges of Safeguards’ compliant file sharing. With document portals secured by 256-bit end-to-end encryption for files in transit and at rest, FileInvite facilitates document collection processes while maintaining bank-grade security.
To learn more about how you can achieve Safeguards compliance in your organization, request a demo, visit FileInvite today.

Related Posts:
- How to send sensitive documents securely via email: Gmail edition
- Is it safe to email tax documents?
- Why Secure File Sharing Matters for Financial Institutions
FAQ's:
How to attach a document in Outlook?
- Click on the "Attach File" button (paperclip icon) in the message header
- Browse and select the file you want to attach
- Click "Insert" to attach the file to your message
How do I access my Outlook drive?
Outlook typically doesn't have a "drive" of its own. It's primarily an email client.
How do I access my Microsoft OneDrive?
- Go to the OneDrive website at https://onedrive.live.com/
- If prompted, sign in with your Microsoft account, you should now be able to access your OneDrive files.
How do I link OneDrive to Outlook?
- Open Outlook and go to the "File" menu
- Click on "Options"
- Click on "Add-ins" in the left sidebar
- Under "Manage", select "COM Add-ins" and click "Go"
- Check the box for "OneDrive for Business" and click "OK"
- Restart Outlook to complete the setup
Why is my OneDrive not syncing?
- Check your OneDrive account to ensure that you have enough storage space
- Make sure that you have a stable internet connection
- Check that your OneDrive app and Windows operating system are up to date
- Try resetting OneDrive by going to "Settings" > "Apps" > "Apps & features" > "Microsoft OneDrive" > "Advanced Options" > "Reset"
- If none of these solutions work, contact Microsoft support for further assistance.
How do I access Outlook data files?
- Open Outlook and go to the "File" menu
- Select "Account Settings" and then "Account Settings" again
- Go to the "Data Files" tab. The location of the data file(s) will be listed under "Filename".
Where are the files for Outlook stored?
The files for Outlook are stored in data files that have the extension ".pst" or "ost". The location of these files will vary based on your operating system and version of Outlook. To find the location of your Outlook data files, you can follow the steps outlined in the previous answer.