37K+
5-star reviews from
FileInvite portal users
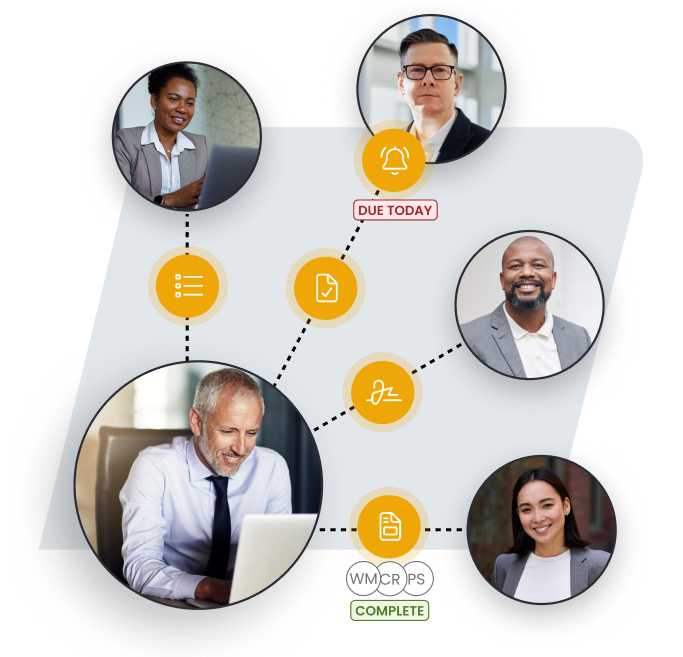
Select contacts, load templates, and send an invite manually or trigger automatically via your CRM
Your borrowers are sent a secure link to upload files, complete forms and sign documents on any device, and receives automatic reminders
Approve or reject documents with one click, or collaborate on a loan application by sharing visibility or assigning tasks to other team members.
Sync documents to cloud storage with smart PDF conversion, standardized naming and organized filing.
5-star reviews from
FileInvite portal users
Files securely collected
Average hours saved
per week, per user
Over 1 million FileInvite
portals served
Standardize complex loan packages with templates that automate requests, reminders, file naming and status updates. AI-powered intelligent email intake automatically matches forwarded documents to the correct customer, loan and request. Get correctly named, complete files faster with less rework, accelerating closings and reducing operational costs. FileInvite runs reliably in the background, making your borrower experience exceptional.
37k borrowers gave us five stars for a reason.


Coordinate document collection across borrowers, guarantors, co-borrowers, brokers, and attorneys. Send party-specific document requests with personalized checklists, track submissions in real-time, and route documents through your internal approval workflows. FileInvite maintains a complete audit trail across all parties, perfect for SBA 7(a) loans, commercial real estate deals, and syndicated transactions.
Assign tasks, share visibility, and collaborate seamlessly across loan officers, processors, underwriters, and credit analysts. Route documents for internal review, add comments and notes on submissions, and mention team members for quick coordination. Set role-based permissions to control who can approve, edit, or view invites, ensuring compliance while keeping deals moving efficiently through your pipeline.
Don't settle for less. A secure and reliable solution, FileInvite is SOC 2 Type II compliant, with 256-bit encryption, advanced user provisioning, and a 99.9% uptime guarantee. Our at rest and in transit encryption ensures that documents, messages and data are secured to the latest security standards. FileInvite is regularly subjected to stringent third party testing.
Choose between open or password protected borrower portals, and tailor internal roles and permissions to suit your security and privacy requirements. Stay compliant with a full history of client interactions, messages and files, and grant access to external auditors when required.
.png?width=723&height=586&name=security-compliance%20(1).png)

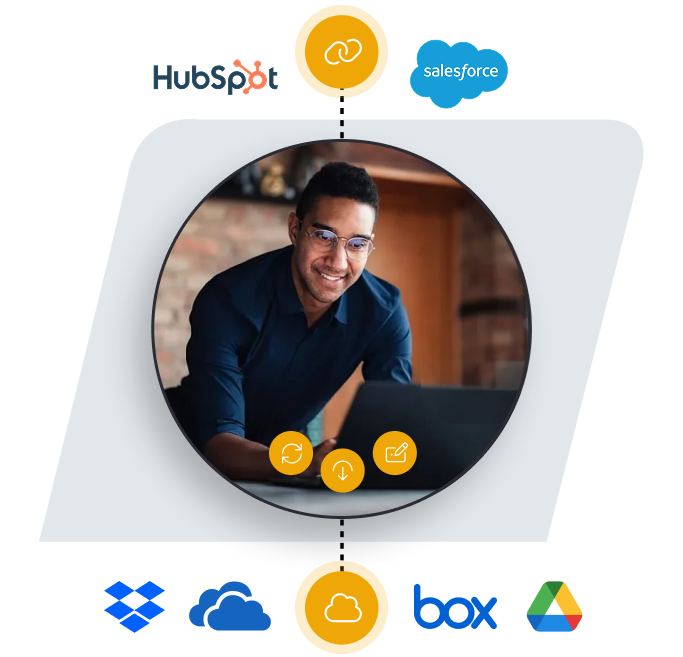
FileInvite's Connected Workflow Integrations allow you to initiate document requests, send messages, and manage workflows directly from Salesforce, Hubspot, and other CRM platforms. Connected Workflow Integrations are a no-code solution implemented by our own teams to speed up delivery and reduce costs and change management.
FileInvite integrates out-of-the-box with cloud storage solutions, including SharePoint, OneDrive, Box and Google Drive, to eliminate manual handling of borrower documents. FileInvite automatically converts all uploaded files to PDF format, securely syncs them to the cloud, and can dynamically rename and organize them to suit your folder and file name conventions.
Unlock a deeper level of integration with FileInvite's enterprise-grade API. Reduce cross-platforming by integrating FileInvite with your core, LOS, or your own internal systems to streamline workflows across multiple applications.



Create a document checklist from pre-built templates or from scratch, send a secure link to borrowers, and they upload files directly to their FileInvite Portal. You receive real-time notifications as documents arrive and can review everything in one centralized dashboard. The process is simple: configure your document requirements for the specific loan type, invite borrowers and any third parties like guarantors or advisors, and they receive clear instructions on what's needed. They can upload documents from their computer or mobile device, add notes or questions, and track their own progress. You can review submissions as they arrive, request clarifications, approve documents, or ask for revisions, all within the platform.
Yes. All plans include custom templates and checklists. Save regular information requests for reuse, sharing, and compliance. Build templates for different commercial loan types including CRE, SBA, construction, commercial lines of credit, equipment financing, and more, each with specific document requirements and custom instructions. Templates can include conditional logic to request additional documents based on loan amount, property type, or borrower characteristics. This ensures consistency across your lending team, reduces setup time for new loan requests, and helps maintain compliance with your underwriting standards. Templates can be shared across your organization or kept private to specific teams.
FileInvite accepts all common file formats including PDF, Word, Excel, and images (JPG, PNG). We also support automatic PDF conversion of uploaded documents and intelligent file renaming based on document type, making it easier to organize and review submissions. Document virus detection is included on all plans to protect your systems from malicious files. Borrowers can upload single files or batch upload multiple documents at once, and there's no limit on the number of files they can submit. Large files are supported, which is important for detailed financial statements, construction plans, environmental reports, and other documentation common in commercial lending.
Yes. FileInvite connects with the tools commercial lenders already use. All plans include native integrations with OneDrive for Business, OneDrive, Google Drive, Box, and Dropbox to automatically sync collected documents to your existing cloud storage. SharePoint is also supported, with files securely synced immediately upon submission and organized into folders for easy navigation. FileInvite automatically converts all uploaded files to PDF format and can dynamically rename them to suit your preferred file naming conventions, eliminating manual document handling.
For CRM connectivity, FileInvite's Connected Workflow Integrations allow you to initiate document requests, send messages, and manage workflows directly from Salesforce, HubSpot, and other CRM platforms. Lenders can trigger document requests automatically when deal stages change, and send and receive messages via the FileInvite borrower portal from within their CRM, maintaining a complete conversation history in one place. These are low-code solutions implemented by FileInvite's own teams, making them fast to deploy without a heavy IT lift.
For deeper connectivity, FileInvite's enterprise-grade API enables custom integrations with your loan origination system, core banking platform, or internal systems, reducing cross-platforming and streamlining workflows across multiple applications. Our Enterprise tier includes dedicated integration support and custom development to ensure FileInvite fits seamlessly into your technology stack. Sign-in integrations with Microsoft and Google are available on all plans for simplified user authentication.
All plans include Smart Notifications. Set due dates when creating document requests, and FileInvite automatically sends friendly email reminders to borrowers at intervals you define, reducing follow-up work for your commercial lending team. You can customize reminder frequency and messaging to match your communication style. Reminders clearly show borrowers what documents are still outstanding and provide a direct link to upload them. This automation ensures borrowers stay on track without your team having to manually track and follow up on every outstanding item.
Yes. All plans support Point of Contact designation, Watchers who receive updates, and free view-only users under a Fair Use Policy. This is essential for commercial lending where deals often involve multiple stakeholders. Premium plans add Teams and Assignees functionality, enabling sophisticated collaboration across guarantors, partners, legal entities, attorneys, accountants, and third-party advisors typical in complex commercial transactions. Each party receives their own secure link and can only see the documents relevant to them, while your team maintains a unified view of all submissions. Internal team members can assign review tasks, add private notes, and collaborate on document evaluation.
All plans include reporting, comprehensive audit trails, and compliance features essential for commercial lending. Track which documents have been submitted, who submitted them, when they were uploaded, and what actions your team has taken. Audit trails provide a complete history of all activity for regulatory compliance and internal reviews. Premium plans add management insights dashboards to help you track average turnaround times, identify bottlenecks in your document collection process, monitor team performance, and analyze trends across your commercial lending portfolio. Export data to identify which loan types have the slowest document collection or which borrowers consistently need the most follow-up.
Yes. All plans include in-portal direct messaging so you can communicate with commercial borrowers directly within the FileInvite Portal without reverting to email. This keeps all communication about document requests in one place, making it easy to reference past conversations and maintain context. You can also add internal team notes that are invisible to borrowers, allowing your underwriters, loan processors, and relationship managers to collaborate and share observations about document quality, missing information, or follow-up needed. All communication is logged in the audit trail for compliance purposes.
Yes. All plans include one-click approve/reject functionality for submitted documents. Review documents directly in the platform, mark them as approved if they meet requirements, or request revisions with specific feedback on what needs to be corrected or supplemented. Maintain a complete audit trail of all document activity and status changes for compliance purposes and future reference. Your team can also flag documents for secondary review, assign documents to specific reviewers, and track which documents have been evaluated versus which still need attention. This structured review process ensures nothing falls through the cracks and provides clear accountability.
Premium plans include a custom branded portal with your financial institution's logo, colors, and styling, plus custom domain options so the portal URL reflects your brand rather than FileInvite. This allows you to deliver a seamless, white-labeled experience that reinforces your brand throughout the document collection process. Borrowers see your branding from the initial email invitation through every interaction with the portal, creating a professional, cohesive experience that builds trust and confidence. Custom domains also improve email deliverability and reduce confusion about the legitimacy of document requests.
FileInvite uses AI to automatically match documents received via email to the corresponding loan request and borrower, eliminating the need for manual sorting and filing. When a document arrives by email, the system identifies what it is and assigns it to the right request, keeping your document collection process organized without adding work for your team. This is particularly useful in commercial lending where borrowers and third parties often default to email when submitting supporting documentation.
FileInvite integrates with the tools commercial lenders already use. All plans include native integrations with OneDrive for Business, OneDrive, Google Drive, Box, and Dropbox to automatically sync collected documents to your existing cloud storage. SharePoint is also supported out of the box, with files automatically synced upon submission and organized into folders. FileInvite automatically converts uploaded files to PDF format and can dynamically rename them to match your preferred file naming conventions, eliminating manual document handling.
For CRM connectivity, FileInvite's Connected Workflow Integrations allow you to initiate document requests, send messages, and manage workflows directly from Salesforce, HubSpot, and other CRM platforms. Document requests can be triggered automatically when deals reach specific pipeline stages, and your team can send and receive borrower messages from within the CRM, keeping conversation history centralized. These integrations are low-code solutions implemented by FileInvite's own teams, meaning fast delivery with minimal change management and no major IT project required.
FileInvite also integrates with Zapier, enabling connections to hundreds of additional platforms not listed above. Specialized integrations include Illion BankStatements, CashDeck, and CreditSense for automated and secure retrieval of bank statement data, and Fortiro Protect for advanced document fraud detection and blacklisting.
For deeper connectivity, FileInvite's enterprise-grade API enables custom integrations with your loan origination system, core banking platform, or internal systems, reducing cross-platforming and streamlining workflows across multiple applications. Our Enterprise tier includes dedicated integration support and custom development. If you don't see a specific integration you need, contact our team to discuss your options.
Coordinate document collection across borrowers, guarantors, co-borrowers, brokers, and attorneys. Send party-specific document requests with personalized checklists, track submissions in real-time, and route documents through your internal approval workflows. FileInvite maintains a complete audit trail across all parties, perfect for SBA 7(a) loans, commercial real estate deals, and syndicated transactions.
Assign tasks, share visibility, and collaborate seamlessly across loan officers, processors, underwriters, and credit analysts. Route documents for internal review, add comments and notes on submissions, and mention team members for quick coordination. Set role-based permissions to control who can approve, edit, or view invites, ensuring compliance while keeping deals moving efficiently through your pipeline.
Don't settle for less. A secure and reliable solution, FileInvite is SOC 2 Type II compliant, with 256-bit encryption, advanced user provisioning, and a 99.9% uptime guarantee. Our at rest and in transit encryption ensures that documents, messages and data are secured to the latest security standards. FileInvite is regularly subjected to stringent third party testing.
Choose between open or password protected borrower portals, and tailor internal roles and permissions to suit your security and privacy requirements. Stay compliant with a full history of client interactions, messages and files, and grant access to external auditors when required.
FileInvite's Connected Workflow Integrations allow you to initiate document requests, send messages, and manage workflows directly from Salesforce, Hubspot, and other CRM platforms. Connected Workflow Integrations are a no-code solution implemented by our own teams to speed up delivery and reduce costs and change management.
FileInvite integrates out-of-the-box with cloud storage solutions, including SharePoint, OneDrive, Box and Google Drive, to eliminate manual handling of borrower documents. FileInvite automatically converts all uploaded files to PDF format, securely syncs them to the cloud, and can dynamically rename and organize them to suit your folder and file name conventions.
Unlock a deeper level of integration with FileInvite's enterprise-grade API. Reduce cross-platforming by integrating FileInvite with your core, LOS, or your own internal systems to streamline workflows across multiple applications.

Coordinate document collection across borrowers, guarantors, co-borrowers, brokers, and attorneys. Send party-specific document requests with personalized checklists, track submissions in real-time, and route documents through your internal approval workflows. FileInvite maintains a complete audit trail across all parties, perfect for SBA 7(a) loans, commercial real estate deals, and syndicated transactions.
Assign tasks, share visibility, and collaborate seamlessly across loan officers, processors, underwriters, and credit analysts. Route documents for internal review, add comments and notes on submissions, and mention team members for quick coordination. Set role-based permissions to control who can approve, edit, or view invites, ensuring compliance while keeping deals moving efficiently through your pipeline.

Don't settle for less. A secure and reliable solution, FileInvite is SOC 2 Type II compliant, with 256-bit encryption, advanced user provisioning, and a 99.9% uptime guarantee. Our at rest and in transit encryption ensures that documents, messages and data are secured to the latest security standards. FileInvite is regularly subjected to stringent third party testing.
Choose between open or password protected borrower portals, and tailor internal roles and permissions to suit your security and privacy requirements. Stay compliant with a full history of client interactions, messages and files, and grant access to external auditors when required.

FileInvite's Connected Workflow Integrations allow you to initiate document requests, send messages, and manage workflows directly from Salesforce, Hubspot, and other CRM platforms. Connected Workflow Integrations are a no-code solution implemented by our own teams to speed up delivery and reduce costs and change management.
FileInvite integrates out-of-the-box with cloud storage solutions, including SharePoint, OneDrive, Box and Google Drive, to eliminate manual handling of borrower documents. FileInvite automatically converts all uploaded files to PDF format, securely syncs them to the cloud, and can dynamically rename and organize them to suit your folder and file name conventions.
Unlock a deeper level of integration with FileInvite's enterprise-grade API. Reduce cross-platforming by integrating FileInvite with your core, LOS, or your own internal systems to streamline workflows across multiple applications.

See how FileInvite helps financial institutions accelerate complex commercial and small business loans, scale volume with existing teams and reduce documentation risk while your loan origination system, document storage and CRM keep doing what they do best.