What's the difference between email and FileInvite?
One of them gets documents back from clients 80% faster (and it's not email).
.jpg?width=600&height=800&name=Untitled%20design%20(8).jpg)
In order to adopt practices that improve information security standards in your organization, it helps to start by identifying what kinds of potentially sensitive information you store and transmit regularly. The kinds of information and documents you should consider sensitive will vary by industry and applicable regulatory controls.
Here are four common types of sensitive information transmitted documents may contain.
When employees exchange or collect documents containing any of the foregoing sensitive information types via email, they should apply protective measures. Here are three steps you can take to mitigate the risk of data breaches in email attachments.
Common document file types such Word docs and PDFs contain password protection features that users can set before attaching documents to emails.
Users can encrypt attachments in popular business email services such as Gmail and Outlook. Users can find these optional settings in the service’s interface for new messages.
In addition to encrypting attachments, users can also encrypt the entire email’s content in many services. Email encryption relies on the Public Key Infrastructure (PKI) paradigm, in which a recipient is assigned a public key stored on a third-party server and a private key for decryption stored on a private server.
Gmail is currently the most widely used business email platform, however very rarely are different security features enabled, event those that satisfy FTC compliance standards for PII. If you are using Gmail, there are a handful of different encryption options you can choose from...
Microsoft Outlook offers some encryption options to increase security, but even sending emails with those options (TLS, S/MIME, or OME) enabled is not always compliant under the FTC Safeguards Rule...
One of them gets documents back from clients 80% faster (and it's not email).
Although password protection and encryption for email attachments reduce the risk of exposing sensitive information to malicious third-parties, these measures cannot eliminate vulnerability entirely. Successful email attack methods still exist and can often result in attackers gaining control over personal computers or software-as-a-service (SaaS) accounts and escalating privileges to gain wider system access.
As defending against these attack vectors depends largely on human behavior — maintaining strong credentials, recognizing phishing and social engineering scams, and not storing sensitive information on unsecured personal devices — organizations that continue to use email attachments as a means of exchanging sensitive information must accept some degree of risk exposure.
Thoroughly eliminating risks involves scrapping email as a file sharing medium and adopting a dedicated secure file sharing platform. Secure file sharing services such as DropBox and GoogleDrive offer users individual and business account types for cloud file storage and exchange.
Not all file sharing services are created equal. Security experts estimate that as much as 40% of SaaS cloud service provider data is unmanaged and exposed to persistent insider threats.
When choosing a service provider, organizations should evaluate the strength of the technologies they employ and the credentials they maintain.
FileInvite is a SOC 2 Type 2 compliant file sharing and document portal platform that protects all data exchanges with 256-bit encryption. Practicing the gold standards of financial information security, FileInvite offers users the highest degree of confidence that their information is protected from all threat types.
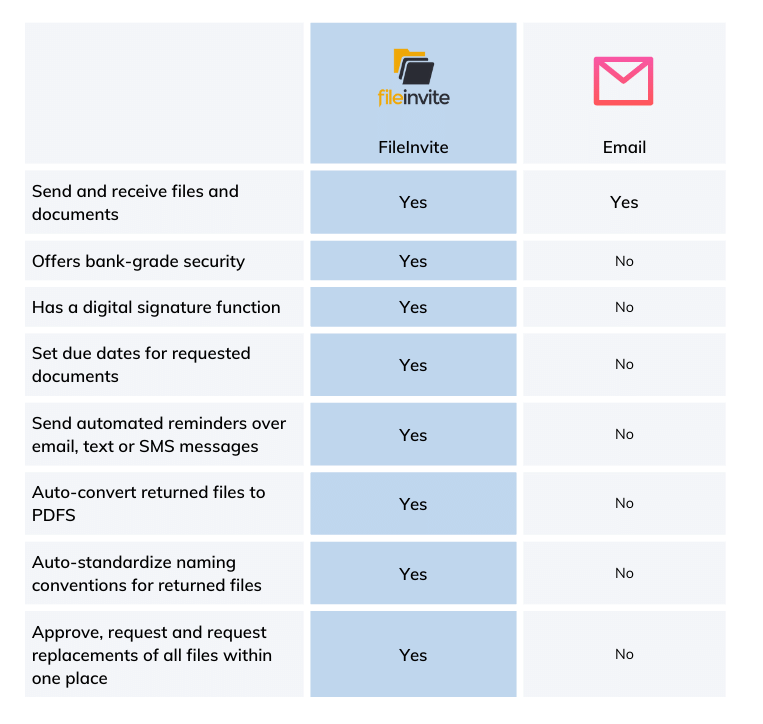
The FTC's updated Safeguard Rule's requirements around encryption, authentication, and customer data disposal expose email’s security shortcomings, and make it no longer a viable solution.
Whether you’re onboarding new clients, or planning to file your own taxes, here are 4 ways to reduce the risks of sharing your PII and PIFI online.
Email as we know it today has been around for 50 years. And while it has evolved in that time, it is essentially still the same thing using the same decades-old technologies, especially when you consider email security.
Gone are the days of requesting documents from clients via email. Our client-facing customers have experienced an average 35% increase in productivity as a direct result of implementing FileInvite.
By improving internal and external efficiencies within the document collection process, the entire lending process moves faster, giving you more time to devote to client - and revenue - growth.
Give your clients complete visibility into the document collection process - including which documents are due and when, as well as what their requirements are. Not only does this increase application completion rates, but it also improves client experience.